January 31st, 2023 by ParadigmSI
By now, most of us are aware of the rising occurrence of ransomware-style cyber attacks. Malicious code is introduced into the enterprise through phishing or some other means, and propagated quickly to infect networks, servers, PC/laptops and other devices.
No organization is immune, and the threat is increasing each year. Large and small commercial companies, as well as state, local and federal governments have all fallen victim to attack. With ransomware, the goal of the cyber criminal is typically financial gain, but may also be an effective means for any other intention that can be used as leverage when your data and systems have been hijacked.
Like any other type of attacker scenario, the ideal victims are those organizations that have left themselves to be vulnerable as easy prey. Loss of access to IT systems and data can be devastating to the under-prepared. Intentional planning, preparedness and prevention are key to thwarting and mitigating these types of attacks.
For the enterprise organization, Disaster Recovery strategies need to be reviewed and updated as necessary to ensure full resiliency. Prevention techniques can begin with an assessment and review of Information Policies and Procedures. A posture review of the IT Systems and controls can be helpful, including timely server patching to stay current with security updates, implementation of proactive antivirus programs, as well as continuous monitoring and intrusion detection solutions.
Within the overall Business Continuity Management Strategy (BCMS) for the organization, it is imperative to identify the resiliency approach for all critical areas or asset classes. Typical assets to be managed for the organization include (but not limited to): Facilities, Personnel, IT/Systems, Data/Records, Supply chain, and Image/Reputation. The BCMS will need to address the “loss of asset” contingency for each of these areas.
In reality, ransomware can potentially affect all these areas, such as access to the Facility, ability for personnel to perform essential functions, management of the supply chain, and certainly loss of image and reputation. When it comes specifically to ransomware and DR strategies, IT/Systems and Data/Records are two of the key asset classifications that can be directly affected by such an attack.
In the case of critical Data/Records, if the primary site becomes infected with malware and you are locked out of these systems, does the organization have redundancy in place, in addition to failover strategies in order to be able to retrieve and operationalize this data? Does this include managed backups and offsite storage? Are these encrypted with full or incremental backups; scheduled hourly, daily or weekly? Are these aligned to the appropriate Recovery Point Objectives (RPOs) for the organization’s critical processes?
For IT/Systems, if the primary site becomes infected with malware and you are locked out of these systems, does the organization have redundancy and failover strategies in place that may include a geographically-dispersed cold-site, warm-site or hot-site? Are these aligned to the appropriate Recovery Time Objectives (RTOs) for the organization’s critical processes that depend on these systems? Depending on the RTO requirements and maximum tolerable downtime for critical processes in the organization, you may require an ‘Active-Active’ level resiliency for a near-real time failover capability as compared to an ‘Active-Passive’ DR strategy.
As sometimes this can be overlooked, be sure to also consider the backup and offsite storage of what is required to run these systems, such as employee pc-image profiles, server images, configuration files and copies of the required software programs with valid license keys.
Once all this is in place, how can you verify the effectiveness of your DR strategy, to include a possible ransomware attack? Many organizations will from time to time facilitate a tabletop exercise to simulate the response procedures for a disruption to the organization. This can be a good start, but be sure to simulate cascading failure scenarios that affect both operational processes as well as related IT/Systems and Data/Records, since most real life disruptions go beyond a single failure point.
Sometimes, instead of a simulated disruption, having a planned and scheduled outage disruption to actually shut down the primary IT systems and bring them back online in an organized manner can reveal the true Disaster Recovery readiness of the organization. Potential gaps will be revealed that may exist in a ransomware scenario when you have been shut out of all your primary IT Systems, programs and data.
The DR strategies required to mitigate against ransomware or any other type of disruption relies on having valid RTOs and RPOs for all the IT/Systems that support the organization. The Business Impact Analysis (BIA) will help you to identify these critical processes, resource and technology requirements, dependencies and operational RTOs and RPOs that will feed into the DR requirements. BC and DR plans can then be developed and documented, including the DR procedures for failover, recovery and restoration that may be needed during a malware or ransomware attack.
What is your level of confidence that you could successfully recover from a test of a primary systems shutdown, or from an actual malware attack? BC/DR planning tools like OpsPlanner™ can assist you and provide an effective foundation to build, plan, document, test, train, mature and continuously improve your organizational resiliency.
For more information about how to better prepare your organization with effective BC/DR Planning tools, or to schedule a tabletop exercise with our Certified Business Continuity Professionals, please contact us via:
- The contact form using the link at the top of this page
- Email at PSISales@ParadigmSI.com
- Call us at 800-558-9568 ext. 300
January 3rd, 2023 by ParadigmSI
Implementing a Business Continuity Management Program
In order for the BCM program itself to be resilient, we must tangibly justify and validate the BCM effort. It is often that this part of the BCM program is neglected.
Before even attempting to define the BCM goals, does your organization have defined Strategic Goals?
For example:

Then, determine the appropriate BCM Goals which have direct traceability back to the organization’s Strategic Goals:
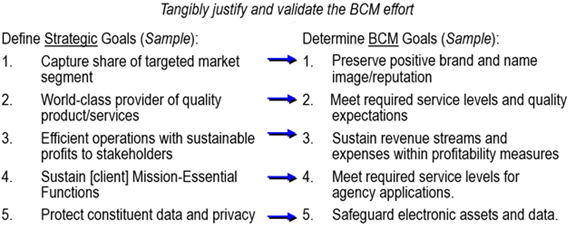
BCM Goals and Metrics should be developed and aligned back to Strategic Goals, then documented as part of the BCM Policy.
Does your organization have defined Strategic Goals that can serve as the imperative for specific and tangible BCM Program goals?
For more information about how to better prepare your organization with an effective Business Continuity Management System and development of BCM Strategic Goals, please contact us via:
- The contact form using the link at the top of this page
- Email at PSISales@ParadigmSI.com
- Call us at 800-558-9568 ext. 300
Coming next month in Part 3: Develop the BCM Policy – Standards & Guidelines
December 19th, 2022 by ParadigmSI
Cybersecurity is a critical part of business continuity management because it helps protect an organization’s information and systems from security threats. A breach of cybersecurity can have significant consequences for an organization, such as the loss of sensitive data, monetary loss, and damage to the organization’s reputation. To prevent these types of disruptions, organizations must incorporate robust cybersecurity measures into their business continuity management plan.
There are several organizations and institutions that offer recommendations and best practices for information and cyber security. Some of the main ones include the National Institute of Standards and Technology (NIST), the International Organization for Standardization (ISO), the Center for Internet Security (CIS), and the SANS Institute.
Here are some examples of recommendations and best practices for information security and cyber security from NIST, ISO, CIS, and SANS:
NIST recommends implementing strong password policies, regularly patching and updating software and security systems, and using encryption to protect sensitive data.
ISO recommends implementing a robust risk management program, including regular risk assessments and implementing controls to mitigate identified risks.
CIS recommends implementing a multi-layered approach to security, including both technical controls (such as firewalls and intrusion detection systems) and non-technical controls (such as employee training and incident response plans).
SANS recommends implementing a defense-in-depth strategy, which involves protecting the network and individual devices at multiple levels to reduce the likelihood and impact of a security breach.
The specific laws that require businesses to keep a degree of cyber security or resilience vary by country and jurisdiction. In the United States, for example, some of the main laws that address this issue include the Federal Information Security Management Act (FISMA), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS).
Here are some examples of what businesses need to do to comply with FISMA, HIPAA, and PCI DSS on cyber and information security:
FISMA requires that federal agencies implement a range of security controls to protect their information and systems, including regular risk assessments, training for employees, and incident response plans.
HIPAA requires that covered entities, such as healthcare providers and insurers, implement technical, physical, and administrative safeguards to protect patient health information. This includes implementing access controls, regular risk assessments, and training for employees.
PCI DSS requires that businesses that accept credit card payments implement a range of security controls to protect cardholder data, such as using encryption, implementing firewalls, and regularly testing security systems.
In general, however, most businesses are expected to take reasonable steps to protect their sensitive data and systems from cyber threats, such as implementing strong password policies, regularly updating software and security systems, and training employees on how to identify and report potential security threats. It’s also important for businesses to have a plan for responding to and recovering from a security breach, to minimize the damage and disruption caused by such an incident.
All-in-all, there are many organizations and institutions that offer recommendations and best practices for information security and cyber security, and there are also various laws and regulations that require businesses to keep a given level of security to protect sensitive data and systems. It’s important for businesses to be aware of these requirements and recommendations, and to implement controls and measures to protect themselves against cyber threats. By following cybersecurity recommendations and best practices, organizations can reduce the risk of a cybersecurity breach and ensure the ongoing availability of their systems and data. This will help organizations keep their overall resilience and ensure their ability to continue working in the face of potential disruptions.
For more information about how to better prepare your organization against cyber-related threats with an effective Business Continuity Management System, please contact us via:
- The contact form using the link at the top of this page
- Email at PSISales@ParadigmSI.com
- Call us at 800-558-9568 ext. 300
December 6th, 2022 by ParadigmSI
The purpose of Business Continuity Management (BCM) is to attain comprehensive operational continuity (ability to continue critical operations during a disruption) and resilience (planning, preparedness and protection over the long-term.)
ref: https://www.iso.org/obp/ui/#iso:std:iso:22300:ed-3:v1:en
In today’s current environment, the global economy is shifting and evolving more now than ever. Geo-political events are disrupting supply chains. Staffing levels and unique staffing approaches are being tested from the COVID-19 pandemic. Infrastructure is becoming more vulnerable with ransomware and other exploits. IT requirements are evolving with the progression of cloud-based systems and the advent of 5G. It will be important that organizations big and small protect themselves from a variety of potential disasters, which will enable them to not only grow but to become sustainable.
What are the drivers for implementation of a BCM program?
The impetus for BCM can stem from external forces such as regulatory requirements (FFIEC or NCUA for financial institutions, etc.) and legal and fiduciary considerations (Sarbanes-Oxley.) Just as well, the drivers for BCM can come from internal factors and stakeholder requirements regarding preservation of the general sustainability and growth of the organization.
Where to begin?
– Establish the BCM Ownership.
To establish ownership and drive the BCM principles throughout the organization, a BCM strategy must be created and approved by the governing board. Ownership must reside at this level as the board owns the overall resilience of the organization, where the CEO and CFO must personally attest to the validity of the data being reported. The BCM Ownership must drive and define the BCM policy in a top-down approach. BCM is difficult to impossible to implement at the grass-roots level.
The BCM Leadership Team will typically include:
– The Business Continuity Steering Committee (BCSC) will be responsible to establish the BCM Policy. The BCSC will provide the appropriate level of authority on those areas of the organization that will most likely be involved with Business Continuity execution.
> At least one Executive, one Senior Management representative, and then what ever level of management is deemed appropriate to represent the full operational components of the organization.

– The Business Continuity Team (BCT) will be responsible to develop and maintain the Business Continuity Plans consistent with the BCM Policy.
> Line-of-Business Leaders, Site Leaders, Program Owners.

Per the ISO BCM standard, persons in top management and other relevant management roles throughout the organization shall demonstrate leadership with respect to the BCMS via demonstration of the following activities:
> Ensuring that policies and objectives are established and communicated for the business continuity management system, which are compatible with the strategic direction of the organization, promote continual improvement, and ensure that the BCMS achieves its intended outcome(s).
> Ensuring the integration of the business continuity management system requirements into the organization’s business processes with: allocation of resources needed for the business continuity management system, communication of the BCMS requirements to organizational staff and stakeholders, directing and supporting persons to contribute to the effectiveness of the BCMS, establishing roles, responsibilities, and competencies for business continuity management, and appointing one or more persons to be responsible for the BCMS with the appropriate authority/competencies to be accountable for the implementation and maintenance of the BCMS as well as supporting other relevant management roles to demonstrate their leadership and commitment as it applies to their areas of responsibility.
Top management shall ensure the parameters and support for the BCMS are communicated within the organization by creating or updating the BCM Policy Document to include:
> Documentation of the Process and Methodology approaches for conducting the organizational BIA and Risk Assessment,
> Documentation of the Process and Methodology approaches for selection of business continuity strategies to protect the critical functions, assets and stakeholders to the organization.
> Defining the criteria for accepting risks and the acceptable levels of risk,
> Actively engaging in exercising and testing,
> Ensuring that internal audits of the BCMS are conducted,
> Conducting management reviews of the BCMS, and
> Demonstrating its commitment to continual improvement.
For more information about how to better prepare your organization with an effective Business Continuity Management System, please contact us via:
- The contact form using the link at the top of this page
- Email at PSISales@ParadigmSI.com
- Call us at 800-558-9568 ext. 300
Coming next month in Part 2: Align BCM to Strategic Goals
December 5th, 2022 by ParadigmSI
Communications can be one of the first readiness conditions that become degraded during a crisis event. Organizational resilience demands effective crisis communications strategies.
The manner and reach of communications has been dramatically altered in this post-pandemic world. Furthermore, increased vulnerabilities to cyberattack and weaknesses in the infrastructure grid require quick and effective solutions to early notification alerting.
What is your level of confidence that your organization can reach out to important stakeholders during a crisis situation?
OpsPlanner can provide your organization with the ability to perform robust emergency notification alerting directly from your activated plan. Since your contact information and lists are already available on your plan, with just a few clicks you can send emergency alerts to all your plan-based Contact lists. You can create pre-defined messages and send alerts to various email, voice or text based recipients using the latest in text-to-speech technology.
With OpsPlanner, the ability to have a comprehensive Emergency Notification Solution (ENS) is easy. There are no third party contracts required, nor the need to maintain and share contact information with another third party database.
For a limited time, Paradigm Solutions International is offering a free 60 day trial of the OpsPlanner Emergency Notification Solution.
For more information about how to better prepare your organization with an effective Emergency Notification Solution, or to sign up for this free 60 day Notification trial, please contact us via:
- The contact form using the link at the top of this page
- Email at PSISales@ParadigmSI.com
- Call us at 800-558-9568 ext. 300
December 1st, 2022 by ParadigmSI
5G is the next generation of mobile broadband service, and it will bring an exponential leap in capability, much more than in previous generations. Ultra-reliable and extreme real-time communications will help to support the growth of the Internet of Things (IoT) down to wearable devices and a massive distribution of sensor networks that will impact the efficiency of our everyday lives.
Currently, the first 5G services are available to about 12% of the mobile broadband users in the US. Within 3 years, 5G coverage availability is expected to be at 25% or greater. 100% coverage availability is expected within four to five years.
The success of 5G will require caching and storing massive amounts of data to support applications and other functions that run on these devices. The advent of smart homes, smart industry and smart cities will require moving a large portion of the computing power down from the cloud to the device level, or closer to the device level.
Edge computing and near-edge computing will be the architecture that is required to support the new mobile broadband ecosystem. Street-level IoT devices and connections, along with micro data centers will fuel the throughput and capacity that is required to enable the middle layer low latency fiber and wireless connections between the core systems that remain in the centralized cloud, and the edge level computing being performed via devices within industry, homes and cities.
5G and Edge computing infrastructure will bring with it many advancements, but also many challenges. Protection of user data and privacy will be paramount. The end user and business consumers will demand increasing capability, capacity, storage and uncompromised security.
While 5G and Edge computing may not dramatically affect your day-to-day consumer functions and business operations today, it most certainly will within a few years to come.
Businesses should be prepared to assess their existing critical functions, data flows, dependencies, and technologies with a view towards the ever-evolving use cases for how users and consumers will interface with your organization, and how your internal BC/DR plans will need to be proactively managed and transformed to meet the needs of the new 5G/Edge computing universe.
Is your Business Impact Analysis (BIA) up-to-date? Does your latest threat assessment include technology and data security hazards? Is your data center and cloud services infrastructure and Disaster Recovery Plan ready to handle the challenges of 5G and Edge computing?
For more information about how to better prepare your organization with effective BC/DR Planning tools, or to schedule a tabletop exercise with our Certified Business Continuity Professionals, please contact us via:
- The contact form using the link at the top of this page
- Email at PSISales@ParadigmSI.com
- For more information, call us at 800-558-9568 ext. 300
- To speak with a Sales Representative about Business Continuity Planning Consulting or Business Continuity Software, please call:814-330-2560





